Abstract
This paper mainly discuss the application of blockchain in secure data storage.
The data is stored off-chain in a distributed way, and the blockchain serves as
an access control list. In the case when a mobile phone application want to
read/write the user's personal data, the verification program must be made and
recorded through the blockchain. In this way, a data owner can surely own and
control their personal data.
Implementation(senario,framework,algorithm)
Framework
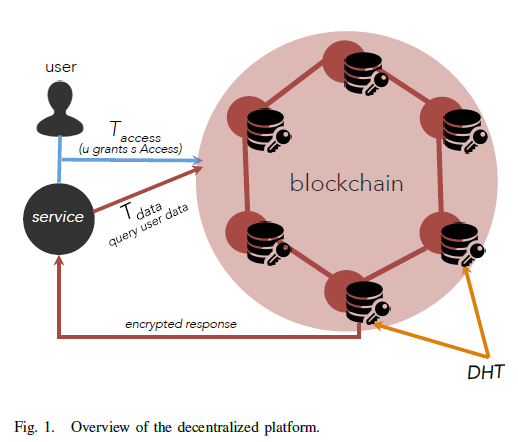
The proposed system focus specifically on mobile paltforms, and consists of three entities, the user, the third-party services and the blockchain, which can ben seen in Fig.1. The user can commit a transaction called T_access which is used to dynamiclly change the access control list and the service can commit the T_data transaction to store or read the user's data.
The Distributed Hash Table(DHT) shows in Fig.1. is the structure for storing data with added an interface to the blockchain. This paper also emphasized the DHT scheme can be replaced by other off-chain solutions, for example, the centralized cloud.
Algorithms and protocols
The concrete protocol include four parts.
- How does the user and the service share some neccessary keys to perform the ACL permission check.
- How does the user commit and store the ACL in the blockchain.
- How does the blockchain executes the ACL permission check when a service want to access the user's data.
- How does the service store and load data after succeed in permission check.
Corresponding to these four problems, there are four different protocols. We introduce the four protocols in a high level.
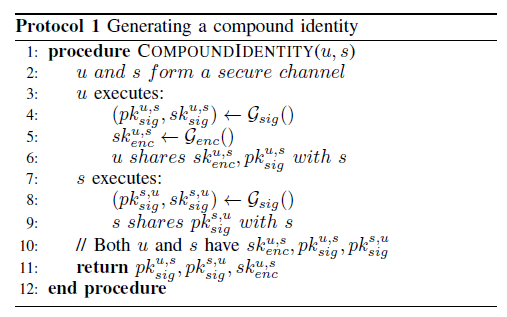
Protocol 1(Generating a compound identity)
The user and a service generate the a <pub,pri> key pairs and send it in a secure channel.
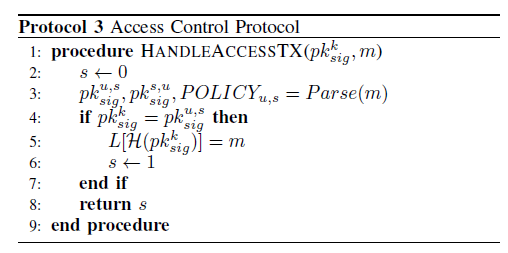
In Protocol 3(Access Control Protocol)
This Protocol is executed when a user commit a T_access transaction, the blockchain first parse the transaction m(Step 3), after a identity authentication(Step 4), the commited POLICY will be stored in the ledger(Step 5).
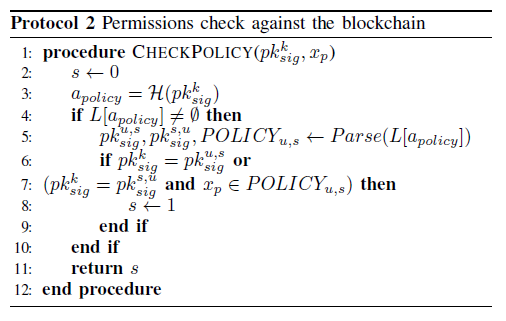
In Protocol 2(Permission check against the blockchain) When a service want to access the user's data, it must first be check by the ACL. The blockchain first retrieve the corresponding policy(Step 3), if the request is made by the user himself(Step 6) or by the service and the service is really given the permission(Step 7), then the ACL permission check succeed, otherwise failed.
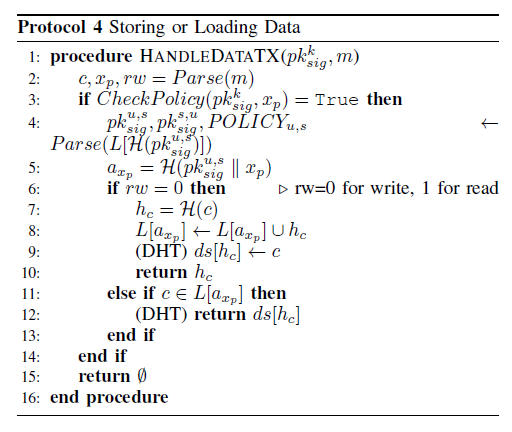
In Protocol 4(Storing or Loading Data)
This Protocol is executed when a service commit a T_data transaction, it first use Protocol 2 to check the permissions(Step3), then using the blockchain to find the address of the data(Step 5), and finally store(Step 9) or loading(Step 12) the data. This paper also explained how to use the Bitcoin blockchain to store and load the data.
The bitcoin transation include a variable number of output address, we can use the first two output as the memory address and the other outputs as a serialized document.
Strong Point(motivation,algorithm,writing)
- This paper introduces the first fine-grained access control mechanism using the blockchain and then the user can totally control their personal data.(motivation perspective)
- This paper writes clearly on how to combine the blockchain with the off-chain storage(a centralized cloud or the DHT).(writing perspective)
Weakness
- This papaer do not have an experiment, so it is hard to say the performance when the service store or loading the data, and the ACL permission check also has an delay.
My point of view
This paper' point of view has been implemented by Enigma and Storj, where Enigma is used for MPC and Stroj is used for distributed storage. The idea of the access control and the reform of the bitcoin transaction output can be surely introduced in verifiable SSE.